AWS Linux LibreSwan VPN Part 3
Contents
Now we can try to connect to an AWS VPN Gateway, using VTI interfaces on Libreswan config and FRR (FRRouting Project) application for BGP routing
Note
There is a related Part 1 and Part 2 section. Please take a look at them if you want to see server preperation steps for Libreswan or policy based IPSEC VPN between two Libreswan gateways
- We are going to create an IPSEC tunnel between “DST GW” and “AWS VPN GW” using VTI tunnel interfaces
- We are going to talk BGP over IPSEC to AWS VPN GW
- We are going to advertise one route through BGP to AWS
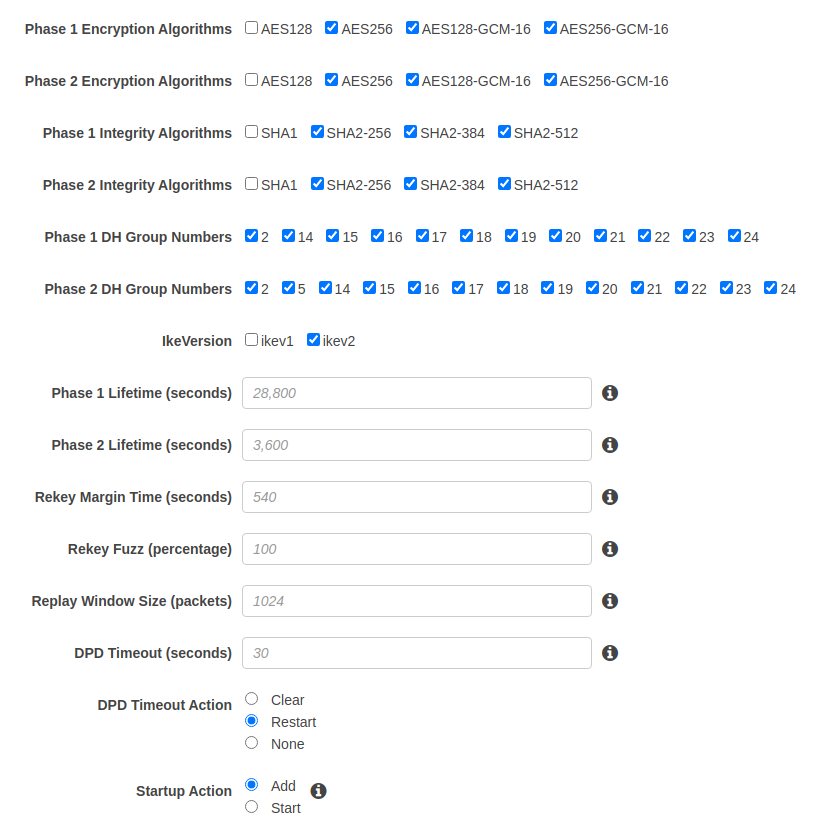
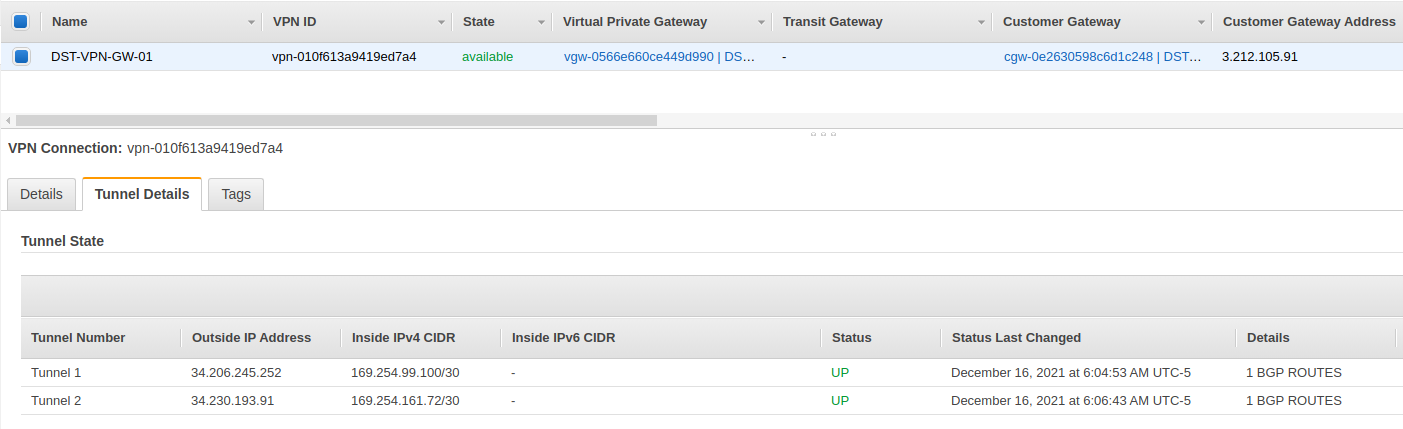
AWS VPN connection settings
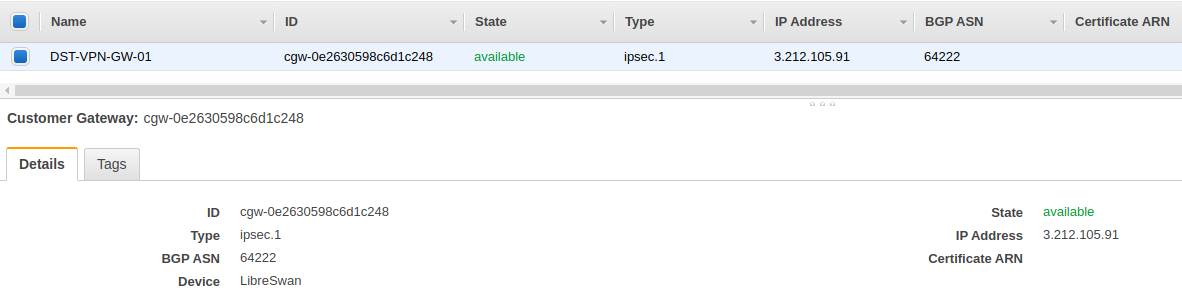
AWS Customer Gateway settings
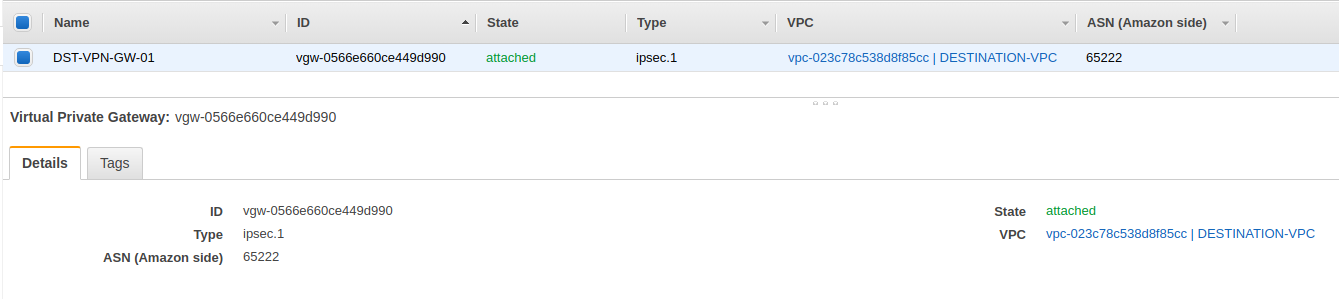
AWS Virtual Private Gateway settings
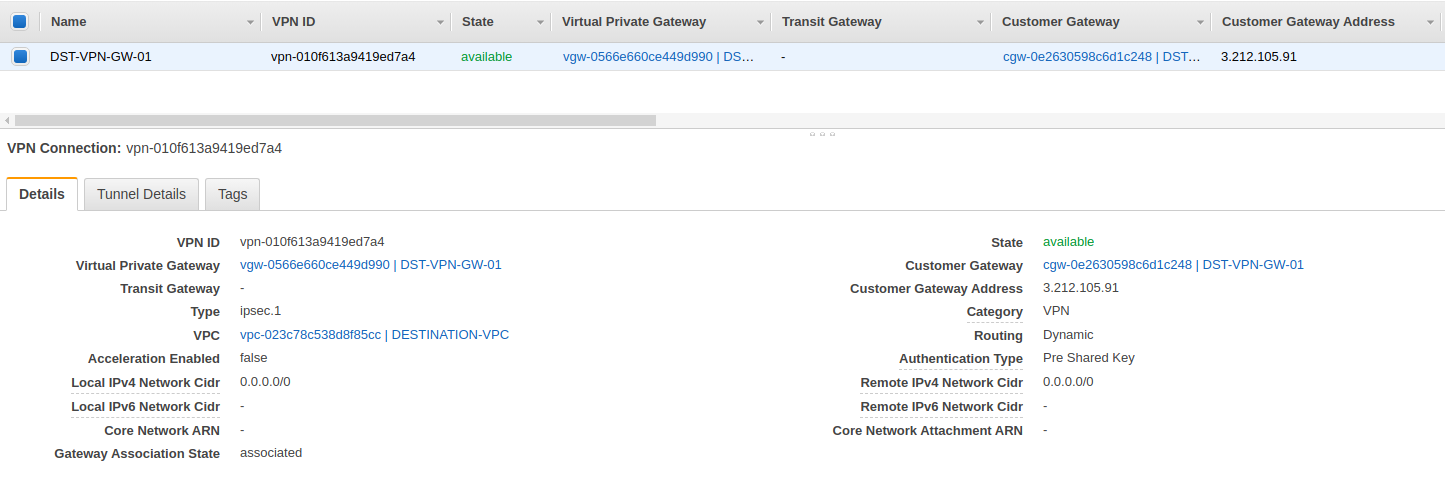
AWS Site to Site VPN settings
FFRouting
We are going to need FRR (FRRouting Project)
$ sudo yum install frr
DST GW
DST GW configuration for the first AWS tunnel
$ cat /etc/ipsec.d/ALL.conf
conn TUN2AWS01
type=tunnel
left=%defaultroute
leftid=3.212.105.91 --> EC2 Instance EIP address
leftsubnets=0.0.0.0/0 --> Reccomended for route based tunnels for minimal number of SAs.
right=34.206.245.252
rightid=34.206.245.252 --> AWS VPN GW IP address
rightsubnet=0.0.0.0/0
ike=AES_GCM_C_256-HMAC_SHA2_512;dh19
mark=5/0xffffffff
vti-interface=vti02 --> Tunnel interface name on RHEL
vti-routing=no
leftvti=169.254.99.102/30 --> Provided by AWS tunnel config
auto=start
pfs=yes
ikev2=insist
fragmentation=yes
authby=secret
ikelifetime=28800s
salifetime=3600s
dpdtimeout=30
dpdaction=restart
aggrmode=no
rekey=yes
encapsulation=yes
DST GW configuration for the second AWS tunnel
$ cat /etc/ipsec.d/ALL.conf
conn TUN2AWS02
type=tunnel
left=%defaultroute
leftid=3.212.105.91
leftsubnets=0.0.0.0/0
right=34.230.193.91
rightid=34.230.193.91
rightsubnet=0.0.0.0/0
ike=AES_GCM_C_256-HMAC_SHA2_512;dh19
mark=7/0xffffffff
vti-interface=vti03 --> --> Tunnel interface name on RHEL
vti-routing=no
leftvti=169.254.161.74/30 --> AWS VPN GW IP address
auto=start
pfs=yes
ikev2=insist
fragmentation=yes
authby=secret
ikelifetime=28800s
salifetime=3600s
dpdtimeout=30
dpdaction=restart
aggrmode=no
rekey=yes
encapsulation=yes
DST GW secrets file
$ sudo cat /etc/ipsec.d/ALL.secrets
3.212.105.91 34.206.245.252: PSK "sZc4886...h6zsdhc2UH"
3.212.105.91 34.230.193.91: PSK "jizW878xEd6...pcyxq"
Check FRR service status
$ systemctl start frr
$ systemctl status frr
$ systemctl enable frr
$ systemctl is-enabled frr
FRR service configuration
$ vtysh
Hello, this is FRRouting (version 7.5).
Copyright 1996-2005 Kunihiro Ishiguro, et al.
dst-vpn-gw-01# show running-config
Building configuration...
Current configuration:
!
frr version 7.5
frr defaults traditional
hostname dst-vpn-gw-01
no ipv6 forwarding
no service integrated-vtysh-config
!
ip router-id 169.254.99.102
ip route 10.111.0.0/16 eth0
!
interface vti02
ip address 169.254.99.102/30
!
interface vti03
ip address 169.254.161.74/30
!
router bgp 64222
bgp log-neighbor-changes
no bgp ebgp-requires-policy
bgp graceful-restart
neighbor 169.254.99.101 remote-as 65222
neighbor 169.254.99.101 ebgp-multihop 255
neighbor 169.254.161.73 remote-as 65222
neighbor 169.254.161.73 ebgp-multihop 255
!
address-family ipv4 unicast
network 10.111.0.0/16
exit-address-family
!
line vty
!
end