AWS Linux LibreSwan VPN Part 1
Contents
Note
First of all few questions
- Why RHEL8 ?
- Because I’m most comfortable with it since I spend a lot of time with RHEL servers
- Why RHEL8 ?
- Because we are going to enable FIPS and it’s really easy to do it on RHEL 8.
- Why Libreswan ?
- It’s a native package comes with RHEL and supported by Red Hat.
- Why FIPS ?
- FIPS is a NIST standard and it’s related to Cryptographic Modules, since we are going to create an IPSEC tunnel we want to use the crypto modules approved by NIST.
Update the server
$ sudo yum update
Change Selinux to “permissive”
$ cat /etc/selinux/config
SELINUX=permissive
SELINUXTYPE=targeted
Enable routing on RHEL kernel
$ cat /etc/sysctl.conf
net.ipv4.ip_forward = 1
kernel settings
Fix few ipv4 settings inside kernel which will be verified by Libreswan
$ cat /etc/sysctl.conf
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.eth0.rp_filter = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.eth0.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.eth0.accept_redirects = 0
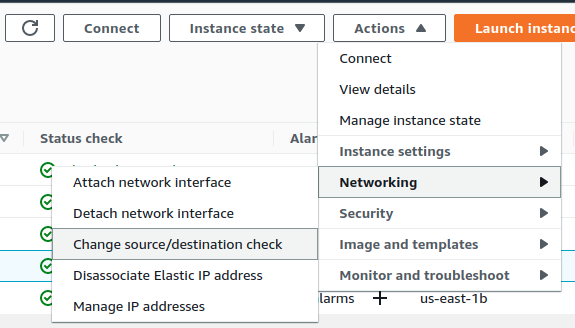
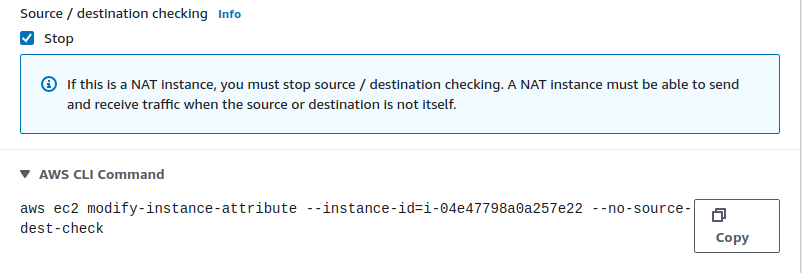
Disable “Source/Destination Check” on EC2 interface
firewalld
Install and enable firewalld service
$ sudo yum install firewalld
$ sudo systemctl start firewalld
$ sudo systemctl status firewalld
$ sudo systemctl is-enabled firewalld
$ firewall-cmd --list-all
Allow ipsec protocol through firewalld
$ sudo firewall-cmd --zone=public --add-service=ipsec
$ sudo firewall-cmd --zone=public --add-service=ipsec --permanent
Enable FIPS (you need to restart server after this step)
$ sudo fips-mode-setup --enable
FIPS
After reboot check if FIPS enabled properly
$ sudo fips-mode-setup --check
FIPS mode is enabled.
LibreSwan
Install libreswan
$ sudo yum install libreswan
Enable libreswan logging with “logfile=/var/log/libreswan_vpngw.log” line inside /etc/ipsec.conf
# cat /etc/ipsec.conf | grep -v "#"
config setup
plutodebug="base"
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
logfile=/var/log/libreswan_vpngw.log
include /etc/crypto-policies/back-ends/libreswan.config
include /etc/ipsec.d/*.conf
Start , check and enable libreswan service
$ sudo systemctl start libreswan
$ sudo systemctl status libreswan
$ sudo systemctl enable libreswan
$ sudo systemctl is-enabled libreswan
Verify libreswan
$ sudo ipsec verify
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 4.4 (netkey) on 4.18.0-348.2.1.el8_5.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Checking rp_filter [OK]
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OK]
Checking 'ip' command [OK]
Checking 'iptables' command [OK]
Checking 'prelink' command does not interfere with FIPS [OK]
Checking for obsolete ipsec.conf options [OK]
Check if libreswan is aware of FIPS enabled kernel
$ sudo ipsec whack --fipsstatus
000 FIPS mode enabled
Nice, we are ready to configure Libreswan IPSEC tunnel now